Are you looking for a Third-Party Risk Management solution, a robust TPRM Policy, or seeking the right third-party risk management tools? This is the article for you.

Every organization depends on more than its internal team to function smoothly—vendors, suppliers, contractors, name it—all support critical operations. But each of these third-party relationships introduces potential risks. A third-party company misconfiguration, a supplier security lapse, or a vendor data breach can destabilize your business operations.
That’s why third-party risk management (TPRM) is no longer optional—it’s indispensable. Understanding and managing third party cyber risk is vital to protect your data, reputation, and bottom line.
In this guide, you’ll get a 360° view of TPRM: from onboarding all the way to offboarding; best practices, continuous monitoring, compliance integration, and even how to evaluate risk score for each supplier. Let’s dive in.
What Is Third Party Risk Management (TPRM)?
Third-party risk refers to the risk posed to an organization by exposure to data breach, negative effects, or being compromised through interactions with third parties and other organizations or parties.
Most organizations use strong IT security systems to protect their internal networks and IT infrastructure but they do not extend their protection to third parties. Nevertheless, third-party relationships significantly contribute to the risk of cybersecurity due to their capability to offer the simple entry into the systems and networks.
This is why third-party risk management exist.
Third party risk management involves a continuous process of risk identification, assessment, monitoring, and mitigation of risks arising due to relationships with the third party- suppliers, vendors, service providers, and contractors, or partners. It is not just a compliance checkbox; it’s a strategic function that:
- Protects sensitive data and systems
- Ensures operational resilience
- Supports your compliance management system
- Prevents reputational damage
As connected digital ecosystems grow, so do the threats. The Kaseya and SolarWinds attacks demonstrated how a single vendor compromise can go multi-organizational.
A robust TPRM program helps prevent that domino effect.
Why is Third-Party Risk Management Important?
Organizations no longer operate in isolation. Whether it is in the form of cloud storage services and payroll providers to marketing agencies and outsourced information technology departments, third-party vendors have become fundamental to the everyday operations of a business. Although these partnerships are beneficial in terms of combating the issue of agility, efficiency, and innovation, they also open fresh avenues of risk, such as cyber risks, operation risks, regulatory risks, and reputational risks.

This is one of the major reasons why Third-Party Risk Management (TPRM) is a strategic imperative.
-
- Exploiting Attack Surface
 Each of the third-party connections presents an additional vulnerability that can be used as a point of attack. IBM Cost of a Data Breach Report 2023 also shows that average data breach involving third parties’ costs $370,000 more than data breach not involving third parties. Third-party cyber risk management makes sure that the vulnerabilities of your vendors do not turn into your next featured breach.
Each of the third-party connections presents an additional vulnerability that can be used as a point of attack. IBM Cost of a Data Breach Report 2023 also shows that average data breach involving third parties’ costs $370,000 more than data breach not involving third parties. Third-party cyber risk management makes sure that the vulnerabilities of your vendors do not turn into your next featured breach.
-
- The pressure of the compliance is increasing.
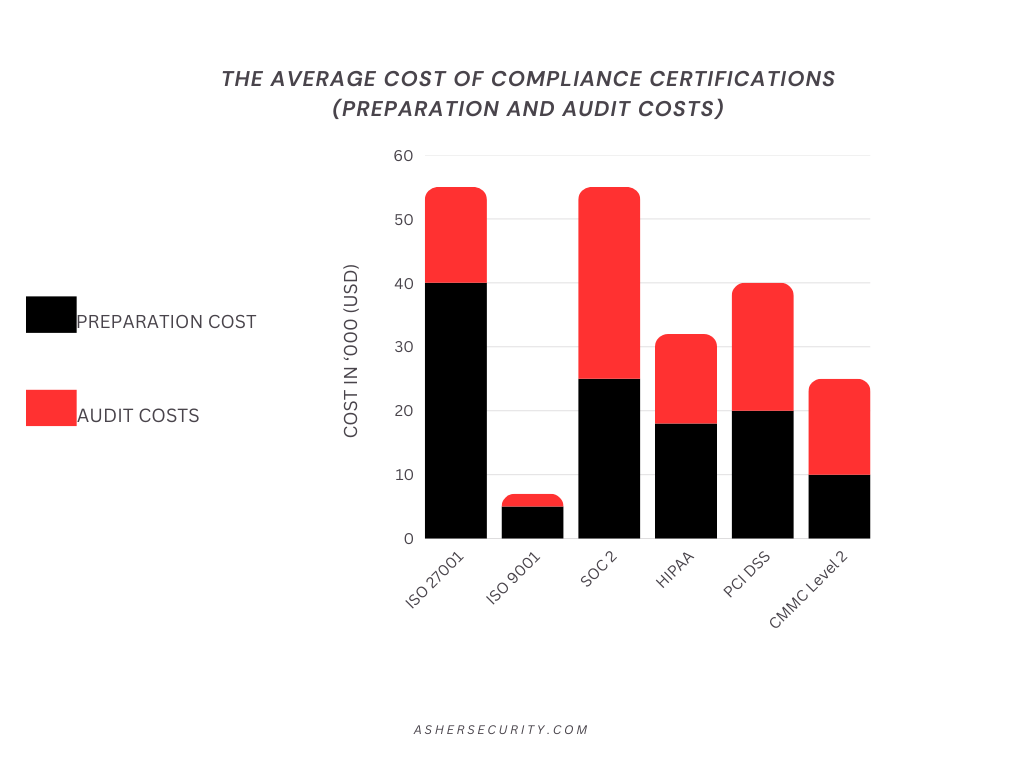 Regulations such as GDPR, HIPAA, CCPA, and SOX are placing a company in jeopardy not only regarding their practices of handling data internally, but also on the actions of their vendors. An effective TPRM framework assists in compliance with a management system, which means that adequate documentation, data privacy, and notification procedures of breaches follow the vendor lifecycle.
Regulations such as GDPR, HIPAA, CCPA, and SOX are placing a company in jeopardy not only regarding their practices of handling data internally, but also on the actions of their vendors. An effective TPRM framework assists in compliance with a management system, which means that adequate documentation, data privacy, and notification procedures of breaches follow the vendor lifecycle.
-
- Avoiding Information Security Breach and Downtime
 Security problems and outages caused by third-party services may result in business down-time at a significant cost and loss of customer confidence. With TPRM policy, you can screen vendors to the best of your ability before you actually hire them and keep an eye out on any red flags-before they cause data breaches or a PR fiasco.
Security problems and outages caused by third-party services may result in business down-time at a significant cost and loss of customer confidence. With TPRM policy, you can screen vendors to the best of your ability before you actually hire them and keep an eye out on any red flags-before they cause data breaches or a PR fiasco.
-
- Constructing Business Resilience
 Third party suppliers or third-party companies work in pivotal roles of supporting business continuity as the globalized supply chains get digital and global. TPRM gives organizations the visibility and responsiveness to react quickly in case a vendor does not perform according to the expected standards, or unexpectedly suffered a cyberattack.
Third party suppliers or third-party companies work in pivotal roles of supporting business continuity as the globalized supply chains get digital and global. TPRM gives organizations the visibility and responsiveness to react quickly in case a vendor does not perform according to the expected standards, or unexpectedly suffered a cyberattack.
-
- Enhanced Risks Prioritization and Score Cards
 An experienced third-party risk management program integrates risk score system, which will help you to determine which vendors are posing the highest risk to your business practices. Risk scoring determines impact and criticality so that a business can identify the resources to invest in mitigation and concentrate on the most essential.
An experienced third-party risk management program integrates risk score system, which will help you to determine which vendors are posing the highest risk to your business practices. Risk scoring determines impact and criticality so that a business can identify the resources to invest in mitigation and concentrate on the most essential.
- Safeguarding Reputation
![]()
 Customer confidence and brand integrity can be hurt by a story of a vendor violation that your organization can have little control over. Third-party risk management can mitigate this exposure by ensuring that any partner has to conform to your threshold of standards of care and transparency.
Customer confidence and brand integrity can be hurt by a story of a vendor violation that your organization can have little control over. Third-party risk management can mitigate this exposure by ensuring that any partner has to conform to your threshold of standards of care and transparency.
Read more on reputation management and vendor score cards: Reputation Management
- Insurance and Incident response support
 Insurers and regulators are demanding to see evidence of third-party risk management as part of the insurability process when considering cyber insurance risk analysis. Having a documented TPRM strategy in place will help to improve your coverage situation and lower your premium amounts and it will help you be ready when the time it’s needed to quickly act in case an incident occurs.
Insurers and regulators are demanding to see evidence of third-party risk management as part of the insurability process when considering cyber insurance risk analysis. Having a documented TPRM strategy in place will help to improve your coverage situation and lower your premium amounts and it will help you be ready when the time it’s needed to quickly act in case an incident occurs.
In Short…
Third-Party Risk Management is critical because it transforms reactive firefighting into proactive risk strategy. With threats increasingly originating outside your organization’s perimeter, a strong TPRM framework isn’t just about vendor control—it’s about business survival, customer trust, and long-term growth.
You can outsource the function, but you can’t outsource the risk. TPRM keeps you in control of your vendor ecosystem, no matter how complex it gets.
What Is the Third-Party Risk Management Lifecycle?
The Third-Party Risk Management Lifecycle is the structured, repeatable process organizations use to evaluate, monitor, and manage risk throughout the entire duration of a third-party relationship—from initial engagement to contract termination.
Understanding this lifecycle is essential to effectively managing third party risk. It enables security teams, compliance officers, procurement leads, and executives to operate from a unified risk lens while keeping the business agile and safe.
Here’s a breakdown of the standard TPRM lifecycle stages:
- Identification & Classification
Begin by creating a complete inventory of your third-party vendors, suppliers, contractors, and service providers. Classify them based on:
- Access to sensitive data or systems
- Criticality to core business functions
- Compliance obligations they impact (e.g., GDPR, HIPAA)
This step helps determine the risk score each party could carry and whether deeper scrutiny is needed.
2. Onboarding & Due Diligence
Before signing a contract, evaluate the vendors:
- Cybersecurity controls
- Data handling practices
- Business continuity plans
- Financial health
- Regulatory history (e.g., past fines, breaches)
Use standardized questionnaires and third-party risk management tools to speed up and automate this process while maintaining thoroughness.
3. Risk Assessment & Scoring
Quantify potential risks by assigning each vendor a risk score using a tailored risk score formula that considers:
- Probability of a data breach
- Impact to operations
- Ease or difficulty of remediation
- Existing controls in place
This step supports smarter risk prioritization—allowing teams to focus resources on third party suppliers that represent the greatest risk.
4. Contracting & Risk Mitigation
Integrate mitigation strategies into the contract stage. This can include:
- Security requirements (e.g., MFA, encryption)
- Data breach notification timelines
- Compliance attestations (e.g., SOC 2, ISO 27001)
- Termination clauses based on risk behavior
Your TPRM policy should define what acceptable security and compliance look like.
5. Ongoing Monitoring
A risk assessment isn’t a one-time task. Monitor vendors regularly using:
- Cyber risk intelligence feeds
- Dark web monitoring for leaked credentials
- Financial performance updates
- Regulatory changes
The right third party risk management solution automates much of this, helping identify shifts in posture quickly.
6. Incident Response Integration
Include third parties in your data breach and incident response plans. Determine:
- What systems are affected
- Who is responsible for response
- How to communicate with impacted stakeholders
For high-risk vendors, test incident response scenarios together at least annually.
Read more on how you can plan your incident response with our vCISO consultant:
7. Offboarding & Termination
When a vendor relationship ends:
- Revoke access to systems and data
- Collect or destroy confidential information
- Review compliance with end-of-life contract clauses
Document the termination and archive records for audit purposes. This step often gets overlooked but is essential in the lifecycle to eliminate lingering access or data exposure.
Key Elements of an Effective Third-Party Risk Management (TPRM) Program
An effective Third-Party Risk Management (TPRM) program is clearly not just a checklist but a business enablement program that enterprises need both to assess, monitor and mitigate the risks posed by their vendors throughout the entire third-party lifecycle. Be it onboarding a new third-party supplier, outsourcing services with a third-party company, or directly integrating a SaaS tool, appropriate foundations are critical to the continuity of your operations along with the security of your operations against cybersecurity threats.

Here are the key pillars of an effective TPRM program:
- Vendor Inventory and Classification
You cannot manage third-party risk until you identify who you third parties are. Begin with an inventory of all third-party vendors that have direct and indirect access to your systems, resources or data. Upon identification, vendors are supposed to be categorized according to the criticality or rather their level of access, their role and contribution to the business. For example:
- Vendors processing PII or financial data = High-risk
- Vendors with system-level access = Medium-risk
- Non-critical suppliers = Low-risk
This classification helps in risk prioritization and determines how much scrutiny each vendor requires during onboarding and ongoing monitoring.
- Standardized Risk Assessment Process
Each vendor should undergo a risk assessment to determine potential vulnerabilities they bring to the business. This process often includes evaluating:
- Data handling practices
- Security controls (e.g., MFA, encryption, patching frequency)
- Compliance with relevant regulations (GDPR, HIPAA, etc.)
- Past history of data breaches or security incidents
Based on risk scoring and a regular risk score formula, company will be able to add each risk level of the vendor by adding a numerical value to the risk level with the help of which better visibility and overall decision making occur. This is of utmost importance when integrating third party risk management tools to automate assessment.
- TPRM Policy and Governance Framework
A documented TPRM policy is the backbone of any effective program. It defines:
- The scope of vendors subject to review
- The frequency of assessments
- Roles and responsibilities (procurement, legal, IT, etc.)
- Escalation procedures for non-compliance or risk findings
This policy should align with the broader compliance management system and be approved at the executive or board level. Clear governance ensures accountability and consistency, especially when multiple departments are involved in managing third-party relationships.
- Due Diligence and Onboarding Procedures
Before signing any contract or granting system access, conduct comprehensive due diligence. This can include:
- Security questionnaires
- Review of SOC 2 reports or ISO 27001 certifications
- Analysis of internal audit findings
- Business continuity and disaster recovery capabilities
Use this phase to determine whether the third-party company aligns with your risk appetite. Automating due diligence with a third party risk management solution can significantly reduce time-to-contract while maintaining control.
- Contractual Safeguards and Legal Controls
Legal agreements must reflect the risk posture of the vendor. Incorporate contractual clauses that:
- Define responsibilities in the event of a data breach
- Require security controls (e.g., patch management, access controls)
- Mandate regular compliance reviews
- Include the right to audit
Having strong legal protections in place doesn’t eliminate risk—but it ensures you have recourse in the event of a failure or breach.
- Continuous Monitoring and Reassessment
Third-party risk isn’t static. A vendor that was low-risk during onboarding may become high-risk after a merger, product update, or security lapse. That’s why continuous monitoring is essential.
This includes:
- Threat intelligence on third party cyber risk
- Real-time alerts for breaches or compliance violations
- Annual or bi-annual reassessments
- Ongoing performance tracking using third party risk management tools
Continuous monitoring enables early detection and proactive mitigation—critical in fast-moving threat environments.
- Incident Response Integration
Vendors should be part of your incident response plan. When a cyber incident occurs, you need to know:
- Who to contact at the vendor’s organization
- What data or systems are impacted
- How to contain and remediate the issue collaboratively
Integrating vendors into your response framework ensures a quicker, coordinated reaction—and minimizes the blast radius of an attack like a web DDoS attack or ransomware incident.
- Training and Internal Awareness
Cyber threat prevention begins with people. Ensure your internal teams are trained to identify and escalate third-party risks. For example:
- Procurement should know how to vet vendors using risk assessments
- Legal should understand TPRM clauses to include in contracts
- IT teams should manage and monitor integrations
Security training for businesses—particularly for employees managing vendors—is a key component of reducing human error and increasing vigilance.
Asher Security Training and Support
- Risk Reporting and Executive Dashboards
Your TPRM program must support executive-level visibility. Dashboards and reports should translate complex risk data into clear, actionable insights.
This includes:
- Risk scores for each vendor
- Changes in vendor risk profiles
- Breach exposure potential
- Policy compliance rate
Metrics should help the executive team make informed, ROI-driven decisions regarding vendor partnerships and investments in mitigation.
- Integration with Enterprise Risk Strategy
TPRM should not operate in a silo. It must align with broader enterprise risk management efforts and strategic objectives. Ensure your TPRM data feeds into:
- Cyber insurance risk assessments
- Enterprise risk registers
- IT governance reviews
- Compliance audits
This holistic approach ensures that vendor risk becomes a part of your overall business risk landscape—not an afterthought.
Conclusion
Effective third-party risk management goes beyond one-off assessments to a lifecycle-driven, risk-based, monitored, and governed approach.
With a strong TPRM policy, appropriate tools, continuous monitoring, and clear ownership, organizations can stay secure without slowing innovation. The question is no longer if you have third-party risk—but how well you manage and control it.
How Asher Security can help
One weak link in your third-party network can trigger a chain reaction — data breaches, compliance violations, and reputational damage that’s hard to undo.
That’s why we created the Rapid Risk Plan — a fast, targeted solution designed to uncover and prioritize vendor-related vulnerabilities in days, not months.
- A clear risk score for each critical third party
- Actionable mitigation steps that align with your compliance requirements
- A roadmap to strengthen your supply chain security without slowing business
In an era where 62% of data breaches are linked to third parties, you can’t afford to wait.
Secure your third-party ecosystem now.
Request your Rapid Risk Plan →
Join the cyber collectives to get the latest news by receiving our monthly newsletter
Tony Asher
Founder, Asher Security • Virtual CISO (vCISO)


Recent Comments