Welcome to our OWASP Top 10 series. This series aims at equipping you with foundational security concerns that exist in today’s cybersecurity landscape. The best resource to use for this is the OWASP Top 10. If you haven’t seen it, take some time to visit the page. It should be one of the primary tools in your tool-belt.
Today we’re looking at Cross Site Scripting, or XSS for short. It’s a code injection attack and very common. It’s been on the OWASP top ten since it started. It’s not called ‘CSS’ because that’s already a web development application, so an ‘X’ is used to indicated ‘cross’.
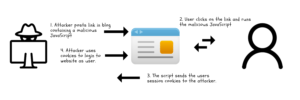
The idea behind an XSS attack is that a vulnerable web application can be leveraged to send a malicious script to the client browser and effectively take data off the client so that the data can be used to perform malicious actions like authenticating to a website.
A vulnerable web application that allows code to be injected into the application can then impact users visiting the web application. When a user visits the site, a JavaScript is executed by the user’s browser. The user’s browser accepts the script because it thinks it’s coming from the trusted web application.
The attack isn’t focused on attacking the website, it’s focused on leveraging a website to attack a user.
The malicious script can hijack session cookies and tokens, or distribute malware.
The main two types of XSS are ‘Stored’ (or persistent) and ‘Reflected’. Stored, also known as ‘persistent’, is a larger threat because it injects the code into the web application where it is stored, thus getting its name. Reflected XSS is not stored in the application, but instead takes advantage of a way to ‘bounce’ the script off the web application onto the client’s browser. This method requires the user to click a link on the page.
Example:
A common way this is performed is that an attacker will post what looks like a comment in a blog, or comment section of a website that is actually a malicious javascript. The visiting user finds the post appealing and decides to click on the link and in doing so actually runs the malicious JavaScript. The script runs on the user’s machine and steals the user’s session cookies and provides them back to the attacker. The attacker can then leverage the session cookies to log in to the web application as a user.
There is a third type of cross-site scripting attack known as DOM-based and leverages the Document Object Model which allows API access to the application code. This attack relies on the client not sanitizing data input.
How to prevent it.
When developing web applications:
-
Input Validation: Make sure that any user input field is performing input validation. Input validation on input fields can prevent JavaScript’s from being entered and posted. White-list inputs, only accepting approved characters and values.
-
Escape: You can also escape user-submitted output. This can be done on the HTML, the URL, JavaScript, and other entry code.
- Sanitize: Lastly you can perform Sanitizing to clean input fields.
When browsing web applications:
- Trust: Only follow links on trusted websites.
- Interrogate: Interrogate hyperlinks to validate they are not malicious. This means not following ‘tiny’ URL’s you’re not sure about, hovering over links to see the destination before clicking or viewing the HTML source code to see what the link is.
I hope this provided a good overview of the cross-site scripting (XSS) attack and equipped you with ways to reduce this risk. If you’re a business that is considering the risk of this in your environment start by looking at your hosted applications. Do you host external, web facing, applications? If so, do you any of those applications allow input from guest users? If so, take the time to sit down with the developer and ask the open-ended question of “what is being done to prevent XSS on this web application?” If they don’t mention things like ‘input validation’, ‘ white-listing’, or ‘sanitization’ I recommend reaching out to us at Asher Security or calling another qualified cybersecurity consultant to review the application for you.
To help reduce the risk of your user credentials being used maliciously, I recommend adding a simple one-page overview on XSS in your security awareness training. Highlight and focus on how to prevent it while browsing the web and following hyperlinks.
Please post any questions or comments below and we will try to respond.



Its such as you read my mind! You appear to grasp a lot approximately this, like you wrote the ebook
in it or something. I think that you can do with
some p.c. to force the message home a little bit, but other than that, that is fantastic blog.
An excellent read. I’ll definitely be back.
I know this if off topic but I’m looking into starting my
own weblog and was curious what all is required to get set up?
I’m assuming having a blog like yours would cost a pretty penny?
I’m not very internet savvy so I’m not 100% certain. Any
recommendations or advice would be greatly appreciated.
Appreciate it
Hermoso reloj digital led KARLSSON para colgar en la pared o poner encima de un mueble.
Esto es debido a que reparte el tiempo del día a la mitad, utilizando la partición AM para la mañana
y la PM para la tarde.
Have you ever thought about publishing an ebook or guest authoring on other blogs?
I have a blog based upon on the same information you discuss and would really like to have you share some stories/information. I know my readers would enjoy your work.
If you are even remotely interested, feel free to send me an e mail.
What a data of un-ambiguity and preserveness of valuable familiarity concerning
unexpected feelings.
Operating system relógios fornecidos pela Loja Suelo vem com certificado de garantia
de 12 meses do fabricante, deixando o cliente seguro para que está recebendo um produto de ótima qualidade.
Hi there everyone, it’s my first go to see at this website,
and paragraph is really fruitful in support of me, keep up posting such articles.
Write more, thats all I have to say. Literally, it seems as though you relied on the video to
make your point. You definitely know what youre talking
about, why throw away your intelligence on just posting videos
to your weblog when you could be giving us something informative to read?
My spouse and I stumbled over here coming from a different web
address and thought I should check things out. I
like what I see so i am just following you. Look forward to checking out
your web page for a second time.
My brother suggested I might like this website. He was totally right.
This post truly made my day. You can’t imagine just how much time I
had spent for this information! Thanks!
Hello there! I simply want to give you a huge thumbs up for the excellent info you have right here on this post.
I am returning to your blog for more soon.
Neat blog! Is your theme custom made or did you download it from somewhere?
A design like yours with a few simple adjustements would really make my blog jump out.
Please let me know where you got your design. Cheers
Thanks for finally talking about > Cross-Site Scripting (XSS):
OWASP Top 10 – Minnesota Cybersecurity Consulting –
Asher Security < Loved it!
Piece of writing writing is also a excitement, if you be acquainted with afterward you can write otherwise it is complicated to write.
It’s actually a nice and helpful piece of info.
I’m satisfied that you shared this useful info
with us. Please keep us up to date like this.
Thanks for sharing.
Very good blog you have here but I was curious if you knew of any
user discussion forums that cover the same topics discussed here?
I’d really like to be a part of group where I can get comments
from other experienced individuals that share the same interest.
If you have any suggestions, please let me know.
Kudos!
Hi, all is going sound here and ofcourse evewry one is sharing
information, that’s in fact excellent, kwep up writing.
Wow, wonderful blog layout! How lengthy have you been running a blogg for?
you made running a blog look easy. The full lok of your website is fantastic, let aloe the content!
Nice post. I learn something new and challenging on websites I
stumbleupon everyday. It will always be interesting to read content from other authors and practice a little something from other web sites.
Do you mind if I quote a few of your posts as long as I provide
credit and sources back to your webpage? My website is in the very same
niche as yours and my users would truly benefit from some
of the information you present here. Please let me know if this alright with you.
Appreciate it!
Thankfulness to my father who shared with me about this website, this blog
is genuinely remarkable.
I read this post completely about the difference of latest and preceding technologies,
it’s amazing article.
Hello there! This post couldn’t be written any better!
Reading through this post reminds me of my previous room mate!
He always kept chatting about this. I will forward this page to him.
Fairly certain he will have a good read. Many thanks for sharing!
Wow! After all I got a webpage from where I can really obtain helpful information concerning my study and knowledge.
I pay a quick visit each day a few websites and blogs to read posts,
but this webpage gives quality based posts.
Hello there! This is my 1st comment here so I just wanted to give a quick shout out
and tell you I really enjoy reading through your blog posts.
Can you recommend any other blogs/websites/forums that go over the same subjects?
Thanks for your time!
Heya i’m for the first time here. I came across this board and I
find It truly useful & it helped me out much.
I hope to give something back and help others like you helped me.
Pretty! This was an incredibly wonderful post.
Thank you for providing this information.
Many thanks! A lot of material!
Best Essay writing
buy essay paper online https://essayservicesall.com