Your ‘risks’ are only as accurate as the ‘threats’ you’ve identified. You need a threat modeling practice.
Introduction
A great cybersecurity program starts with the foundational ability of determining cyber risk. Although there is a not a certified, industry standard equation to determine cyber risks, I will offer the model I use.
Data (value) x Vulnerability x Threat = Risk
In this simple equation we can quickly identify the importance of accurately determining what applicable threats influence our overall risk determination.
I’ve personally witnessed the threat identification discussion being skipped and cybersecurity teams quickly jumping to risks. Sometimes this is due to inaccurate use of how risk is defined, and other times it’s an attempt of quickly filling in the blank so they can get back to doing what they enjoy doing.
Breaking down this risk equation there are three areas we need to identify to accurately determine risk and they are;
Data (value): I recommend this is the result of a data classification exercise. The way I do this is review the company organization chart, and interview key business stakeholders and ask them what data would they grab if the building was burning. Then I follow up by asking where they store that data, and what applications do they use that data for. The result is a data classification policy that identifies all key data elements that are highly classified, or should be labeled ‘Restricted’. A count of the number of data types (PII, SSN, chemical compounds, contract agreements, pricing models…) gives the scale of the data and then record count of each of these gives you the volume of classified data.
Vulnerability: This information is easily collected by a vulnerability management program that can scan all the assets in scope and produce a report of how many critical, high, medium, and low vulnerabilities exists. This can either be a part of an existing program, or a one-time scan can be conducted. Note it is critical to include all assets and endpoints, not just user workstations.
Threats: This brings us to the core of this article, about how to identify threats to complete your risk equation.
What is Threat Modeling?
Threat modeling is a core fundamental concept of cybersecurity. Threat modeling is the discipline of qualifying what threats, and threat actors, can act against your network, applications, or systems. It’s the practice of modeling how the tools, techniques, and tactics could be used against you and introduce risk, so that you can consider and respond to the potential outcomes of that attack.
What Threat Modeling is NOT
Threat Modeling is not a product or technology you can look up on the magic quadrant and call your technology reseller and purchase. It’s not a product.
That’s refreshing. I’m all for great products to help the program, but it’s process that is at the foundation of a great cybersecurity program. This is a key process that will help determine and measure risk.
Why Should You Threat Model?
You should practice threat modeling so that you can determine and prioritize what threats are appropriate to consider into your risk equation, and to prioritize your cybersecurity initiatives based on the historical prevalence and current threat landscape of events.
How to Get Started Threat Modeling
Threat modeling at its core is the considering of threats that exist and identifying which ones apply to you, and if so, how critical are they.
There are two basic ways to perform threat modeling. The first is manual, and the second is automated.
Manual
Manual threat modeling starts by assessing the landscape and listing threats you feel are applicable. You can do this by reviewing the news, or threat intelligence, your historic incident records, or leveraging an already created risk catalog.
HITRUST does offer a Threat Catalogue you can leverage, but at the time of this writing it appears you have to fill out a form to gain access.
Once you have a list of threats to consider, review each one with a team. This can be two or more other people and plot the risk on a impact chart. An impact chart will map threats by impact by measuring likelihood on one plane, and impact on another plane. The goal of plotting the threats to identify the ones with the highest impact and likelihood. Those are your top threats.
Here is an example of threat impact chart I developed for a client:
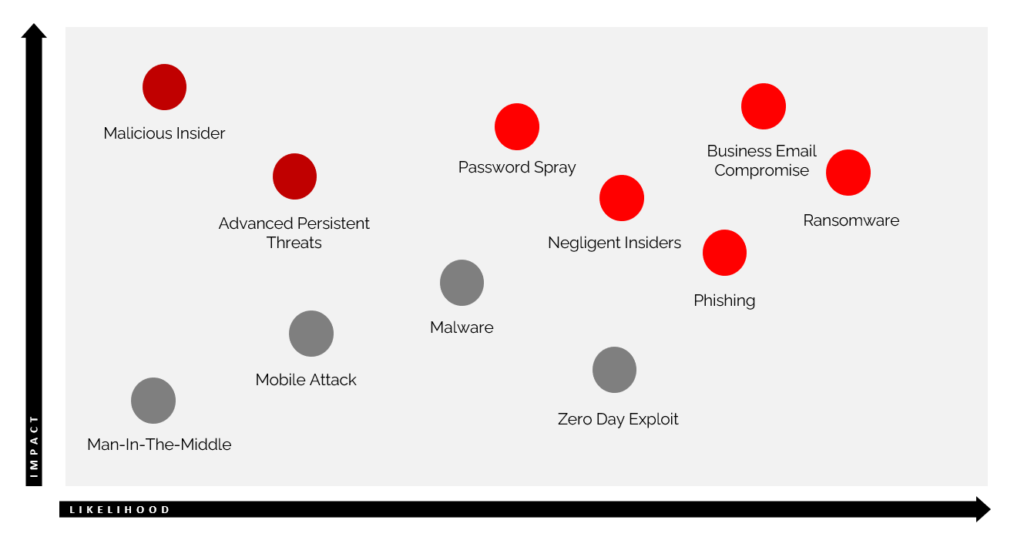
Automated
There are automation tools that can help identify threats and perform threat modeling. Remember when I said you can’t buy threat modeling? Well, that is still true, but applications like IriusRisk is an online application that can help your process.
There are several automation tools you can use. Some of the most popular are:
- STRIDE: https://en.wikipedia.org/wiki/STRIDE_%28security%29
- Microsoft Threat Modeling Tool: https://docs.microsoft.com/en-us/azure/security/develop/threat-modeling-tool-getting-started
- IriusRisk: https://www.iriusrisk.com/
- Threat Modeler: https://threatmodeler.com/
- OWASP Threat Dragon: https://owasp.org/www-project-threat-dragon/
Keep in mind threats can pertain to anything, so scoping your threat modeling exercise is helpful when determining which tool is the best fit for you. Some tools can be used to determine environmental threats, while others are specifically scoped for web applications.
While I haven’t preformed threat modeling for physical environment or data centers, I typically focus on cloud hosted environments, and web applications.
To perform automated threat modeling for this scope the key ingredient is an architecture diagram. I’m going to be transparent here so you don’t get upset later, most teams I’ve worked with to develop a threat modeling program do not have an accurate or up to date architecture diagram. Some teams have offered me one, but it’s more of a flowchart or a data flow diagram.
The ideal diagram will be one that shows technologies, protocols, interfaces, and security boundaries.
If you can’t get access to one of these, don’t be disappointed, you’re already improving the cybersecurity program by working with the technology team to develop and document one. This practice alone brings up great discussion, discoveries, and improvements.
If you can get one, then you can start working with a tool like IriusRisk by creating an account. The free community edition offers the ability to build one model for no cost. It’s a great way to get started.
To get started with a tool like IriusRisk you’ll start building the architecture model within the IriusRisk application, much like you build a diagram with a tool like Visio. IriusRisk offers templates for different technologies and tools you can literally drag from the working panel onto your diagram, and then draw a line that represent a communication channel or security boundary. As you build out your model with the tool it will begin to list all the threats that are applicable to your model. The more details you add, the more accurate and prioritized the threat model is.
IriusRisk takes this even further by mapping the threats to vulnerability information and exploit data and even recommending ways to remove or reduce the threats.
Using the tool is a learning curve. For me that learning curve was half pushing into a new process, and the other half the application use itself. Because I hadn’t used a tool, or modeled like this before my mind kept falling into a groove how I thought it should work. I needed to break those habits and stay disciplined until it started to make sense.
Review the Threats
Once you have a list of applicable threats from your manual effort that was plotted don an impact chart, or a list of applicable threats form an automation tool like IriusRisk, review them with the cybersecurity stakeholders and ensure that they make sense and you all agree on them.
Perform a short exercise of identifying which threats are easiest to remove or reduce. This quick effort can provide exponential value and provide a return on risk investments. A few small changes or updates can greatly influence your risk equation.
Update Your Risk Equation
Once you’re clear on your threats, you now have the final remaining component for your risk equation. Congratulations.
The scope of computing the values of your risk equation is beyond this article, and I will try to write something on that effort. Bottom line is that when you can identify your threats, and you’ll be able to overlay them with your vulnerability data and ask are these important? And then overlay that information with your Data component by asking if this threat were to exploit this vulnerability, will it expose this Restricted data? If you can answer yes, you’ve got yourself a severity one, smoking hot risk that needs to be prioritized, escalated, and addressed.
Follow your cybersecurity risk treatment process. For me, this means getting visibility of this risk by showing the cybersecurity governance committee and proposing risk treatment. After that, ensure the risk gets added to the risk register.
Summary
Building a threat modeling practice doesn’t have to be difficult. Starting with a manual list and reviewing it and then maturing to an automation tool will build your program that shows you know how to identify a key component of risk, prioritize it, and perform it in a repeatable way. This key data will provide clarity on how risk can be reduced for your organization.
Get Started
If you want to learn more about how to get started building a threat modeling practice, I recommend these resources:
- Book: Securing Systems by Brook S.E. Schoenfield
- LinkedIn Learning – Adam Shostack (https://www.linkedin.com/learning/instructors/adam-shostack) ‘
- YouTube: Threat Modeling in 2021 with Adam Shostack (https://www.youtube.com/watch?v=7jB5OS6mepU)
Offer:
If you want help building a Threat Modeling practice for your cybersecurity program, I’m happy to help by introducing you to my partners that I have worked directly with to help my clients get off the ground, build awareness, training, and grease the model.


Recent Comments