Cybersecurity Risk Management Strategies Every Organization Needs
The vCISO Playbook

Understanding the Value of Cyber Risk Management in 2025
Risk management isn’t theoretical. The average cost of a data breach now exceeds $4.88 million, and the cost is rising, particularly when third-party vendors or supply chains are involved. Add to that the cost of lost productivity, compliance violations, and brand damage—and the ROI of effective risk management strategies becomes clear.
Mitigation is almost always cheaper than recovery.
But effective risk management doesn’t happen by accident. It requires structured risk assessments, real-time threat identification, and actionable mitigation strategies. This is where Virtual CISO (vCISO) services come into play—offering businesses, especially small to mid-sized organizations, the guidance and governance typically delivered by a full-time Chief Information Security Officer, without the overhead.
Let’s dive into the specific strategies that enable businesses to protect their assets, prioritize vulnerabilities, and build a stronger cybersecurity foundation using the insights of a virtual CISO.
But before that…
Asher Security Virtual CISO services
At Asher Security, our approach to cyber risk begins with a clear objective: identify, prioritize, and mitigate risks in a way that’s structured, transparent, and aligned with business goals.
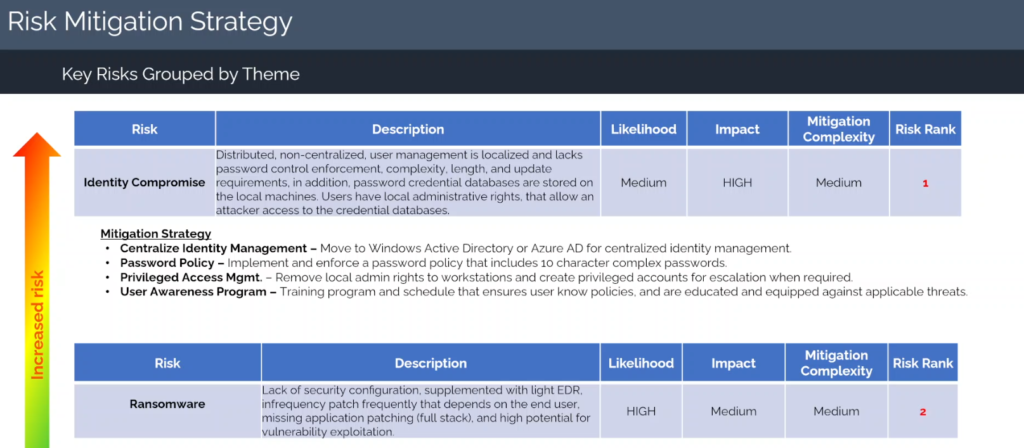
Here is a risk mitigation strategy that we use at Asher Security to help our clients decide which risks to take on first and how to take them on. This synonymized report was prepared as a result of our rapid risk assessment (Email us to get a full clear copy or our strategy)
In this guide, we’ll walk through the risk management strategies we use during our rapid risk assessments, covering everything from initial threat vulnerability risk assessment to mitigation techniques and executive reporting. Whether you’re aiming to tighten your defenses, reduce compliance risk, or improve your cybersecurity governance, risk, and compliance (GRC) strategy, this roadmap is designed to help.
Risk Management Strategies One: Prioritizing What Matters
Every successful risk management strategy starts with prioritization. This is where a risk register becomes invaluable. That means knowing not just what the risks are, but which ones matter most based on their likelihood, impact, and mitigation complexity.
We start with a risk register, a structured document that logs all known cybersecurity risks—often between 40 and 100. From there, we rank the top 10 critical risks based on a calculated risk score that combines likelihood and impact, and then we assign a priority level.
But here’s the key: although the vCISO leads this process, final say on ranking belongs to the business stakeholders. Why? Because no one understands the internal context better than the organization itself. They know which assets are irreplaceable, which functions drive revenue, and where unaddressed risk could cause the most damage.
“A Virtual CISO can advise and rank, but the business always has the final word on risk appetite.” Tony Asher
With the guidance of a vCISO, this register is continuously updated through both qualitative and quantitative methods. The output? A color-coded risk matrix that visualizes organizational risk posture in a way that resonates with executives and board members—balancing technical insight with clear communication.
“Numbers are a great way to bridge the gap between cybersecurity specialists and executive decision-makers. A visual risk matrix brings clarity to complexity.”
Building a Resilient Strategy
Before an organization can manage risk, it must first understand it. This begins with a comprehensive risk assessment—a systematic process to identify, evaluate, and prioritize potential threats.
A high-quality threat vulnerability risk assessment involves mapping assets (data, systems, users), evaluating current security controls, and then calculating both the likelihood and impact of potential threats. This step lays the groundwork for an effective risk analysis, which is used to drive decisions about resource allocation and risk response.

Risk Management Strategies Two: Define and Describe the Risk Clearly
Once prioritized, each risk must be clearly described. A vague label like “Identity Compromise” means little on its own.
Here’s an example of how we flesh out such a risk:
Title: Identity Compromise
Description: User accounts are managed locally on endpoints with no centralized control. Password policies are absent—no complexity, no expiration, and users have admin rights on their machines. Credential databases are stored locally and unencrypted, making them a prime target for attackers who gain access through phishing or malware.
This descriptive step adds vital risk analysis context, helping both technical and non-technical stakeholders understand the root causes of the risk.
Risk Management Strategies Three: Score Likelihood, Impact, and Mitigation Complexity
Every risk is then scored in three key areas:
- Likelihood: How probable is it that this risk will materialize?
- Impact: If it does happen, how damaging will it be?
- Mitigation Complexity: How difficult or resource-intensive will it be to resolve?
These scores, typically ranked on a scale of 1 to 5, are multiplied to calculate a priority score (e.g., 5×5 = 25, the highest priority). This methodology supports a more data-driven risk assessment, making it easier to allocate resources wisely.
Risk Management Strategies Four: The Mitigation Techniques
A strong risk management strategy is only as good as its mitigation techniques. It’s not enough to identify threats vulnerability; organizations must take decisive action to reduce or eliminate them.
Let’s explore a real-world scenario:
A vCISO identifies identity compromise as a high-risk issue. Users have local administrator access, weak password policies, and credentials stored in unsecured local databases.
A detailed mitigation plan may include:
- Centralized identity and access management (IAM)
- Enforcing strong password policies (complexity, rotation, length)
- Implementing privileged access management (PAM)
- Launching a user awareness training program
These mitigation strategies aren’t just theory—they’re chosen based on feasibility, urgency, and alignment with the organization’s current tech stack and capabilities.
Each step is designed to reduce the likelihood and impact of the identified risk while aligning with the organization’s resources and security maturity. This tactical layer is vital—not just for data breach protection, but for ensuring long-term resilience.
Risk Management Strategies five: Build a Risk Register and Maintain It
A risk register is not a one-time document—it’s a living system that evolves alongside your organization. It includes:
- Risk title and description
- Likelihood and impact scores
- Mitigation complexity
- Assigned ownership
- Remediation status
- Timelines for resolution
For small businesses especially, keeping this register lean—focusing on the top 10 high-impact risks—can make all the difference in execution. After those are addressed, new risks can be elevated and prioritized.
Risk Management Strategies Six: Visualize Risks with a Risk Matrix
Now, it’s time to communicate. And nothing communicates better with executives than a risk matrix.
This grid maps the number of risks against severity and probability, often color-coded:
- Red = Critical
- Orange = High
- Yellow = Medium
- Green = Low
A risk matrix is one of the most effective ways to convey risk posture in cybersecurity governance meetings, board briefings, or audits. It simplifies complex technical risks into a format executives understand and can act upon.
“Numbers are the universal language between cybersecurity pros and business leaders.”
Data Breach Response Planning: Be Ready, Not Reactive
Despite best efforts, no system is impenetrable. That’s why having a data breach response plan is as crucial as preventing breaches in the first place.
A comprehensive response plan includes:
- Clear reporting and escalation procedures
- Defined roles for internal and external stakeholders
- Communication templates for legal, PR, and affected users
- Regular tabletop exercises and simulations
A vCISO can ensure the plan aligns with regulatory requirements (e.g., GDPR, HIPAA) and that your team knows exactly what to do when every second counts.
This reduces downtime, protects your reputation, and significantly lowers the average cost of a data breach—which often escalates due to delayed responses or confusion during incidents.

Preventing Cybersecurity Fraud in Small Organizations
Cybercriminals often target small businesses because of limited defenses. A tailored plan with steps to prevent cybersecurity fraud in a small organization might include:
- Conducting regular risk assessments
- Implementing two-factor authentication (2FA) across accounts
- Training employees on phishing and social engineering
- Monitoring third-party vendors and enforcing security SLAs
- Performing regular software updates and vulnerability scans
This is where vCISO services truly shine—offering scalable, right-sized security solutions that provide enterprise-grade protection to smaller teams with modest budgets.
Consistency and Communication Are Key
Lastly, keep your process repeatable, consistent, and simple. Executives need regular updates in familiar formats. A standardized risk matrix, consistent terminology, and a clear remediation roadmap create confidence and buy-in.
Anticipate executive questions like:
- “Which risks are highest priority?”
- “What are we doing about them?”
- “What do you need from us?”
When you can answer those clearly and consistently, you’re not just managing risk—you’re leading it.
Why a Virtual CISO is Your Cybersecurity Catalyst
Whether you’re developing your first risk management strategies or refining a mature cybersecurity program, a vCISO brings clarity, leadership, and hands-on support.
With the rising complexity of digital ecosystems—and the growing risk posed by cloud misconfigurations, AI misuse, and vendor vulnerabilities—a virtual CISO provides:
- Deep experience across industries and frameworks
- Objective, third-party assessments and guidance
- Strategic alignment between security and business goals
- Enhanced communication with leadership and boards
- Streamlined execution of risk mitigation techniques
Need a trusted partner in your risk journey?
Let’s talk about how our vCISO services can help you strengthen your strategy, reduce your risks, and build a resilient future.

Tony Asher
Or Join Our Monthly Newsletter
Join our inner circle (Cyber Collective) for early access to new collections, curated insights, and stories you won’t find anywhere else.

Recent Comments