
In today’s fast-evolving cyber landscape, one-size-fits-all security no longer cuts it. With threats and data breach growing more targeted and sophisticated by the day, organizations need clarity, not chaos—especially when it comes to assessing risk. Organizations now face layered, persistent threats — from supply chain vulnerabilities and insider risks to AI-generated phishing and ransomware-as-a-service. A well-structured cybersecurity risk assessment isn’t just about finding flaws; it’s about creating a repeatable, scalable strategy for prioritizing what matters most.
According to the 2025 Verizon DBIR, nearly 70% of breaches involved human error, misuse of credentials, or third-party vulnerabilities—emphasizing just how critical it is to understand where your organization stands. Public safety and critical infrastructure sectors have been among the hardest hit, pushing agencies and enterprises alike to rethink how they approach security assessments.
This is where the Cybersecurity Risk Assessment Funnel comes in.
Inspired by operational frameworks and field-tested insights (including those from CISA’s Cyber Security Evaluation Tool and SAFECOM’s risk guidance), this 4-step funnel simplifies the overwhelming into the actionable. It’s designed to help security leaders focus on what’s relevant, filter out noise, and move from discovery to decision with confidence.
Let’s break down each stage—and show you how this funnel can help your team build smarter, more resilient cybersecurity practices from the ground up.
Who to turn to for cybersecurity risk assessment
 A well-structured, repeatable risk assessment funnel is vital. At Asher Security, we’ve helped clients—from mid-market firms to regulated enterprises—translate cybersecurity chaos into clarity using a streamlined four-step funnel process. It’s designed to make risk assessments more meaningful, measurable, and actionable, no matter where you are in your security maturity journey.
A well-structured, repeatable risk assessment funnel is vital. At Asher Security, we’ve helped clients—from mid-market firms to regulated enterprises—translate cybersecurity chaos into clarity using a streamlined four-step funnel process. It’s designed to make risk assessments more meaningful, measurable, and actionable, no matter where you are in your security maturity journey.
In this blog, we’ll break down the four key phases that guide our cybersecurity consulting services (virtual CISO/vCISO) team when building risk assessments. From Process, People, Policy , and Security Standards to how they work together to drive smarter, more resilient security.
4-Step Strategy for Cybersecurity Risk Assessment
Step 1: Building the Funnel
Every solid risk program begins with clarity: what are we trying to protect, what could go wrong, and how badly would that hurt? This step is about building a process that goes beyond box-ticking. It means designing a system that gathers, organizes, and prioritizes risk data in a consistent and meaningful way.
a) Identifying the digital assets
The first activity in the funnel is identifying the digital assets you want to protect — data, systems, third-party integrations, and business processes. According to CISA, risk assessments should begin with a comprehensive understanding of “what’s at stake,” including public image, critical service functions, and mission continuity.
A robust assessment process includes:
- Data flow mapping
- Asset inventory
- Business impact analysis
- Threat intelligence gathering
You’ll want to leverage risk registers to document these findings. Every risk entry in your register should have a title, detailed description, likelihood, impact, and mitigation complexity.
Why Risk Identification Matters
Too many assessments fail because they start from assumptions instead of evidence. A rushed or incomplete identification process can lead to missed blind spots, overinvestment in low-impact threats, or underestimation of high-impact vulnerabilities. For example, identifying ransomware as a general risk isn’t helpful unless you understand where ransomware could actually enter your environment — whether it’s through phishing emails, exposed RDP ports, or outdated third-party apps.
A Virtual CISO (vCISO) can help cut through the noise by using a consistent framework for uncovering risks across your environment. That includes both technical vulnerabilities (like unpatched systems or misconfigured firewalls) and non-technical threats (like untrained employees, vendor weaknesses, or poor access controls).
What to Consider During Risk Identification
Here’s what you should uncover during this first phase:
- Data Risk: What sensitive information do you store? (e.g., PII, financials, IP)
- Business Systems: Which systems or applications are mission-critical?
- Threat Sources: Who might target your data? (e.g., cybercriminals, insiders, nation-states)
- Vulnerabilities: What security gaps already exist in your infrastructure?
- Third-Party Exposure: Which vendors and integrations could introduce risk?
According to the 2025 Verizon DBIR, third-party involvement in data breaches doubled from 15% to 30% year-over-year — highlighting how external partners can expand your risk landscape just as much as internal systems.
b) Prioritize with Purpose
Rather than treating all risks equally, score each one based on:
- Likelihood: How probable is this to occur?
- Impact: What’s the worst-case scenario if it does?
- Mitigation Complexity: How difficult will it be to fix?
Scores are usually assigned on a 1–5 scale and multiplied. A score of 25 (5×5) becomes your high-priority risk — typically marked in red in a risk matrix for visibility.
Example: Identity compromise via distributed local admin accounts and poor password hygiene. If users are the primary firewall and have elevated privileges, the risk of database compromise becomes critical.
Prioritization enables meaningful resource allocation and sets the stage for executive decision-making. And this is where cybersecurity consulting services adds real value — translating highly technical findings into boardroom-ready risk matrices.
Pro Tip from Our cybersecurity consulting services (vCISO) Playbook
Start small but go deep. Focus on one application or business unit at a time. Map out its data flows, users, and dependencies. Then ask: What could go wrong — and how bad would it be if it did?
Step 2: People – Empowering Human Accountability
Even the best-designed process will fall apart without clear ownership.

A risk assessment funnel needs people — not just participants, but leaders. Risk owners must be identified at every layer. These are often department heads, system owners, or executive stakeholders who have the authority to act on risk findings.
Map Roles to Risks
Start by assigning:
- Risk Owners: Responsible for signing off on risk responses
- Assessment Leads: Often IT or vCISO roles conducting the work
- Governance Sponsors: Executives or boards who will receive reports
This mapping helps eliminate silos. Far too often, assessments are completed, then shelved — not because the risks aren’t real, but because no one was clearly responsible for acting on them.
A strong vCISO will not only coordinate this mapping but also ensure it aligns with internal reporting structures and regulatory frameworks.
Why This Matters
The 2025 DBIR highlighted that human errors and misconfigurations are still leading causes of data breaches. Yet in many organizations, the same teams that discover the problems aren’t empowered to fix them.
That’s where clearly defined roles, combined with executive support, make a difference. With a cybersecurity consulting services (vCISO) facilitating these relationships, risk moves from being “someone else’s problem” to “everyone’s responsibility.”
Step 3: Policy – Turning Influence Into Governance
Cybersecurity leaders often rely on influence to drive change. But as assessments expand and risks multiply, influence alone isn’t enough.
You need policy.

From Favor to Standard
If you’re asking stakeholders to take action based on risk findings, you must define whether it’s a favor or a standard. Favors require influence. Standards require enforcement.
That’s the power of a cybersecurity policy framework. By implementing policies such as:
- Risk assessment mandates
- Data classification rules
- Third-party vendor guidelines
- Incident response procedures
…you shift from optional to operational. Policies turn influence into governance, and they ensure repeatability in future assessments — regardless of who’s on the team.
Tailoring the Policies
Policies don’t need to be lengthy — but they do need to be clear. A one-page policy that defines:
- What qualifies as a “critical system”
- How data must be categorized
- How frequently assessments must occur
…will do more to streamline future risk work than hours of meetings.
Cybersecurity Consulting Services or vCISOs can help draft these policies and align them with compliance requirements such as ISO 27001 , NIST CSF, or SOC 2. This ensures policies serve dual purposes: internal governance and regulatory assurance.
Step 4: Security Standards – Defining the Baseline
Security standards are the practical counterpart to policy. If policy says “this is what we expect,” standards say “this is how we’ll do it.”

Think of them as blueprints. They define the specific settings, integrations, and controls that must be implemented to keep risk within tolerance.
Sources of Security Standards
Most standards fall into one of three categories:
-
Industry Best Practices
These include frameworks and benchmarks such as:
- CIS Benchmarks (especially for operating systems)
- NIST 800-53 control sets
- ISO 27001 Annex A controls
These published standards are critical references. Instead of arguing “why” a control is necessary, you can reference existing best practice.
-
Company Cultural Standards
What does your organization already expect? These might include:
- MFA for all external logins
- SOC 2 attestation for vendors
- Network segmentation by data sensitivity
By codifying these expectations into standards, you create consistency across assessments.
-
System-Specific Requirements
Each platform introduces unique risks. Take Salesforce, for example. While Salesforce provides strong controls, the way it’s configured can introduce vulnerabilities.
vCISOs review User Control Considerations (UCCs) and define standards for:
- Session timeout
- Password complexity
- Access provisioning
- Data residency and export settings
Instead of starting from scratch each time, security standards give your team a launchpad — and reduce the burden of technical re-analysis.
Why Security Standards Matter
Think of security standards as the policy lens through which you evaluate whether a risk is acceptable or not. Without these predefined benchmarks, every risk assessment becomes a subjective debate. One team might think an issue is urgent, while another sees it as minor. That misalignment slows down remediation, weakens accountability, and reduces the credibility of your cybersecurity program.
According to IBM, only 24% of generative AI initiatives are properly secured — largely due to a lack of clear, enforceable standards on how those technologies should be configured, accessed, and governed. Without standards, even the most well-intentioned security assessments turn into guesswork.
What Should Influence Your Security Standards?
Building effective standards doesn’t mean starting from scratch. Most organizations will define them based on three critical inputs:
-
Industry Best Practices
Use published frameworks such as:
These standards offer a trusted starting point for common platforms and technologies — and help reduce friction when justifying security requirements to internal stakeholders or external auditors.
-
Company Culture
Internal expectations matter. If your organization already enforces certain controls — like MFA for external apps or SSO integration— those should be reflected in any system-specific security standard. This ensures new systems or vendors don’t inadvertently lower your overall security posture.
-
Technology-Specific Risks
Every application introduces unique security needs. A CRM platform may need field-level data encryption and role-based access controls. A financial reporting system might require stronger audit logging and backup protocols. This is where a vCISO brings huge value — helping translate abstract security principles into actionable, platform-specific requirements.
What This Looks Like in Practice
Let’s say you’re assessing a new SaaS vendor. Your security standard might include:
- SOC 2 Type II attestation
- SSO integration using your IdP (like Okta)
- Mandatory MFA for all admin roles
- Data encryption in transit and at rest
- No use of production data in dev/test environments
Instead of debating these items later, you present them upfront — creating transparency and reducing back-and-forth.
Pro Tip from Our vCISO Playbook
Document repeatable security standards by system type (e.g., SaaS, on-prem, vendor-hosted). This helps avoid rebuilding expectations every time you run a risk assessment and enables faster evaluations.
Score Likelihood, Impact, and Mitigation Complexity
Risk scoring methodology is a critical step that brings objectivity, prioritization, and direction to your cybersecurity risk strategy.
Why risk Scoring methodology Matters
Not all risks carry the same weight. Some may be highly likely to occur but cause minimal disruption, while others might be rare yet devastating. To make informed, strategic decisions, you need to assess:
- How likely is this risk to occur?
- How damaging would it be if it did?
- How difficult is it to fix or mitigate?
By scoring each of these areas and calculating a total risk score, cybersecurity leaders can focus resources where they’re needed most — instead of being trapped in reactive firefighting mode.
The Risk Scoring Methodology Framework
At Asher Security, our vCISO teams typically score risks on a scale of 1 to 5 across three key dimensions:
-
Likelihood
This measures the probability of the risk materializing. Is the vulnerability easily exploitable? Has it happened before? Does your threat intel suggest it’s on the rise?
Example: A system without MFA where phishing emails are common may score a 4 or 5 in likelihood.
-
Impact
This reflects how damaging the risk would be if it occurred. Could it expose customer data? Shut down operations? Violate regulations?
Example: A credential leak that provides access to financial records might score a 5 in impact.
-
Mitigation Complexity
How difficult or resource-intensive would it be to fix the issue? Some risks are low-hanging fruit — like turning on a setting — while others may require major architectural changes.
Example: Moving from local admin rights to least privilege access across all endpoints might be a 4 in complexity.
These scores are multiplied to generate a priority score. For instance:
- plaintext
- CopyEdit
- Likelihood (4) x Impact (5) x Mitigation Complexity (2) = 40
This scoring formula is part of our vCISO playbook, helping clients quickly identify their Top 10 Risks and allocate budgets and efforts effectively.
Visualizing Risk: The Risk Matrix
To make this process even more executive-friendly, we use a risk matrix — a grid-based chart that plots each risk based on likelihood and impact. The result is a visual representation of your threat landscape, color-coded for clarity:
- 🔴 Red = Critical Risks
- 🟠 Orange = High Risks
- 🟡 Yellow = Medium Risks
- 🟢 Green = Low Risks
This allows board members and stakeholders to grasp the urgency of risks at a glance — and enables CISOs to communicate clearly without getting lost in technical jargon.
Statistic to note: According to IBM’s 2023 Cost of a Data Breach Report, organizations that didn’t use a risk-based prioritization approach spent an average of $1.76 million more per breach than those that did.
Pro Tip: Don’t Aim for Perfection
Risk scoring methodology is part science, part judgment. As Tony Asher says,
“You’re putting these numbers in to try to come up with this… these are best guesses based on your experience and training.”
Your goal isn’t perfection — it’s consistency and transparency, allowing your risk management decisions to be understood and trusted across teams.
Develop a Risk Mitigation Strategy and Track Progress
Identifying, prioritizing, and scoring risks is essential — but it’s only meaningful if it drives action.
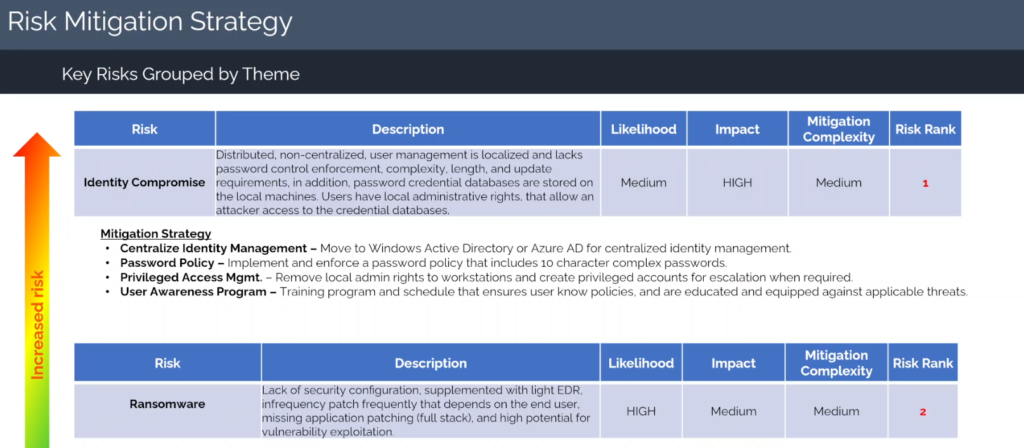
This final step in the cybersecurity risk assessment funnel is where insights become outcomes. Once your top risks are clearly prioritized, your focus should shift to developing pragmatic, measurable risk mitigation strategies and ensuring they’re implemented and tracked over time. (Email us to get a full clear copy or our strategy)
Turning Risk into Action
Each risk you’ve scored should now have a corresponding risk mitigation plan. This isn’t just a list of “nice-to-haves.” It’s a tactical playbook for how your organization will reduce risk to an acceptable level — or eliminate it entirely.
Example: If the highest-ranked risk is related to identity compromise, your risk mitigation strategy might include:
- Centralizing identity management (e.g., Azure AD or Okta)
- Enforcing password policies and complexity requirements
- Implementing least privilege access
- Launching a user awareness and phishing training program
Conclusion on Cybersecurity Risk Assessment Funnel
The Cybersecurity Risk Assessment Funnel gives leaders a clear, repeatable framework to do just that. By focusing on Process, People, Policy, and Security Standards, you transform your risk assessment from a static checklist into a dynamic, decision-driving system. One that not only uncovers vulnerabilities but also empowers your organization to act on them — with clarity, speed, and confidence.
Whether you’re starting from scratch or refining your current risk strategy, this 4-step funnel ensures your efforts are prioritized, your team is aligned, and your security posture is future-ready.
Cybersecurity isn’t just about stopping threats. It’s about building resilience, gaining executive trust, and creating a security culture that lasts.
Ready to take the guesswork out of your cybersecurity strategy?
Let our vCISO experts help you turn insights into action. Whether you’re building from the ground up or refining your risk processes, we’ll help you align people, policies, and standards to strengthen your defenses — and your business.
⇒Join our inner circle (Cyber Collective) for early access to new collections, curated insights, and stories you won’t find anywhere else.
Tony Asher
Founder, Asher Security • Virtual CISO (vCISO)


Recent Comments