In this article I’m going to walk through my approach using Microsoft Security Center and what steps you can take to immediately reduce risks associated with having Azure cloud.
Microsoft defines Cloud Security Posture Management (CSPM): identifies and remediates risk by automating visibility, uninterrupted monitoring, threat detection, and remediation workflows to search for misconfigurations across diverse cloud environments/infrastructure, including: Infrastructure as a Service (IaaS).
Reference: https://www.microsoft.com/en-us/security/business/security-101/what-is-cspm
There have been a lot of cybersecurity incidents that have exploited cloud mis-configurations. These range from weak passwords, lack of multi-factor authentication, and open data repositories.
For Azure cloud users, Microsoft offers a built-in dashboard that helps administrators improve their cloud security posture and prevent cloud mis-configurations that can lead to identity hijacking, and data exfiltration. They currently call it the Security Center. For companies with an appropriate Microsoft license it can be found at https://security.microsoft.com/
The score is an aggregate of 63 recommended security controls.
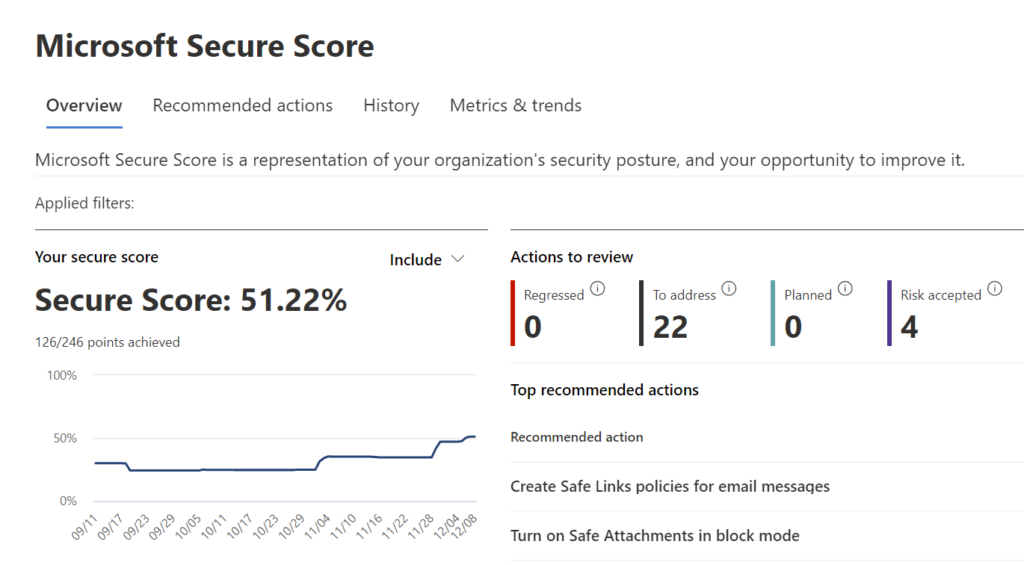
For companies that don’t have this feature included in your license suite, I strongly recommend you get it or identify a different CSPM to implement.
Expectations
I’m my hardest critic. So, investing time in Microsoft Security Center and not getting a 100% score can be disappointing. That’s why I want to set some expectations for you before we get started:
- You won’t achieve 100% – Set a realistic goal. Talking with consultants and professionals that specialize in Microsoft cloud security, they have told me 55% is great score to active for users with E3 licenses, and 75% is a great score for users with an E5 license.
- Your penalized on things you don’t own – That’s right, many features that are required to get higher scores might not be included in your license suite. Licensing is still confusing to me, but when working with Microsoft Security Center it becomes even more frustrating trying to achieve a score when you logically cannot without purchasing more features.
- Overlooked – I’ve experience many times making a recommended security improvement only to return to the security score dashboard later and not seeing a score improvement. I believe there might be some bugs within the system that prevent a consistent way of confirming the improvements.
- Unable to Enable – Sometimes the existing security architecture in place will prevent you from enabling recommended features. For example, if you’re not using Microsoft as your cloud identity broker, and instead have enabled multi-factor authentication (MFA) on that third-party platform, you will not want to enabled MFA in Microsoft Azure.
Approach
Export the Data and prioritize
The first thing I recommend is exporting the list of recommendations Microsoft provides and prioritizing them, instead of working within the security dashboard.
To do this, click on ‘Improve Score’ on the Security dashboard, or ‘Recommended actions’. This screen on the dashboard will provide a list of actions you can take to improve your security score. Find the ‘Export’ option and download the list into a spreadsheet format.
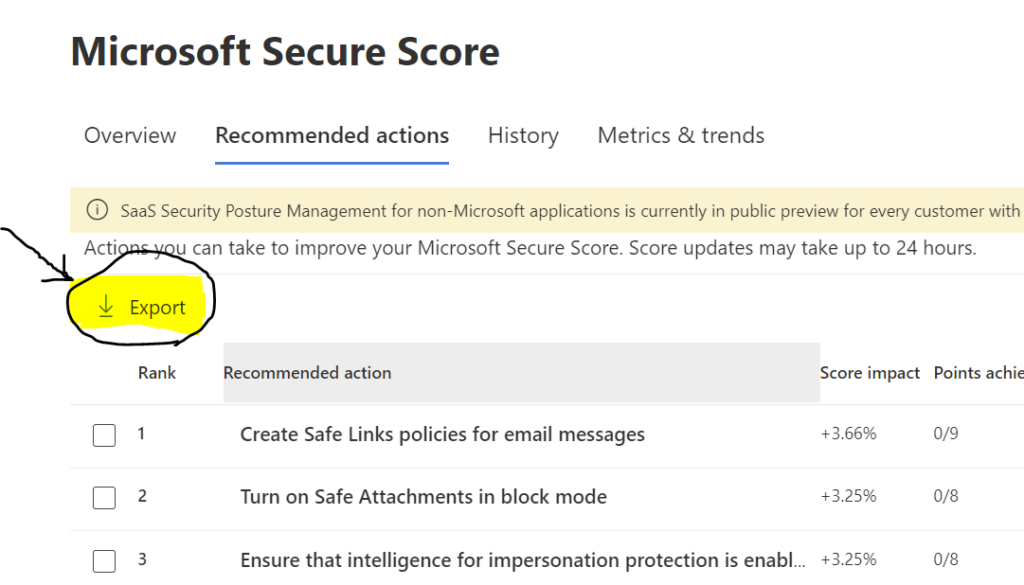
Open up the CSV file and do the following:
- Delete the following columns (these fields are not helpful for this exercise):
- Regressed
- Category
- Product
- Last synced
- Microsoft Updates
- Filter the top row
At this point it should look something like this:
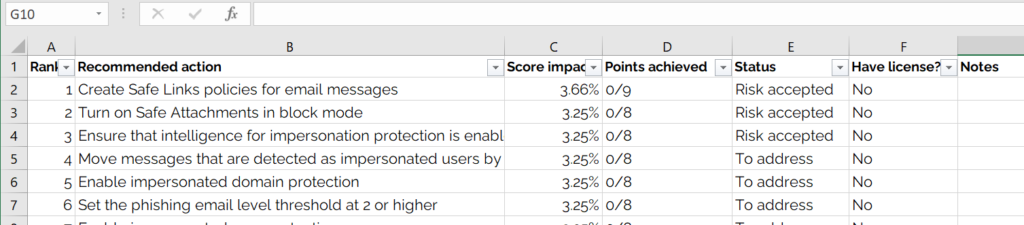
- Filter the ‘Have license?’ column for “Yes” This will show you what controls you have the ability to actually change. (We’ll get to the “No” later).
- Prioritize the remaining (filtered) controls based on ‘Score Impact’. You can do this by just visually scanning the results, or by applying a ‘Sort’ formula.
- Highlight the top 10 highest impact ‘Recommended Actions’ in red, and the next ten in yellow if it helps you visually identify your top priorities.
This exercise takes you from a looking at a dashboard and feeling overwhelmed and maybe uncertain where to start, to a clear and prioritized list of specific actions to focus on.
Redundant Controls
For Microsoft Security Center controls and recommended actions that you don’t want to implement you can still get credit by documenting remediation actions.
This is common for companies that have a third-party identity broker in front of Office 365, and Azure with Single Sign On enabled. Before completing the mitigation documentation to receive credit for the control, ensure the remediation is in place by performing the following:
- Single Sign-On Redirect: Attempt to log in directly to the following URLs;
- myaccount.microsoft.com
- office.com
- Administrative portals:
- https://admin.microsoft.com/
- https://portal.azure.com
Warning: Be careful as I’ve often seen companies require SSO on the Office portal, but not include the Azure portal. You definitely want to include the Azure port.
- Multi-Factor Authentication: If attempting to login to the URL’s above successfully redirects you to the company’s third-party identity broker, attempt to login and ensure you’re prompted for multi-factor authentication.
Once you’ve ensured SSO and MFA are successfully in place you can remediate several of the Microsoft Security Score Recommended Actions;
# 21 Enable self-service password reset
# 27 Require multifactor authentication for administrative roles
# 28 Ensure all users can complete multifactor authentication
To remediate these controls, perform the following steps:
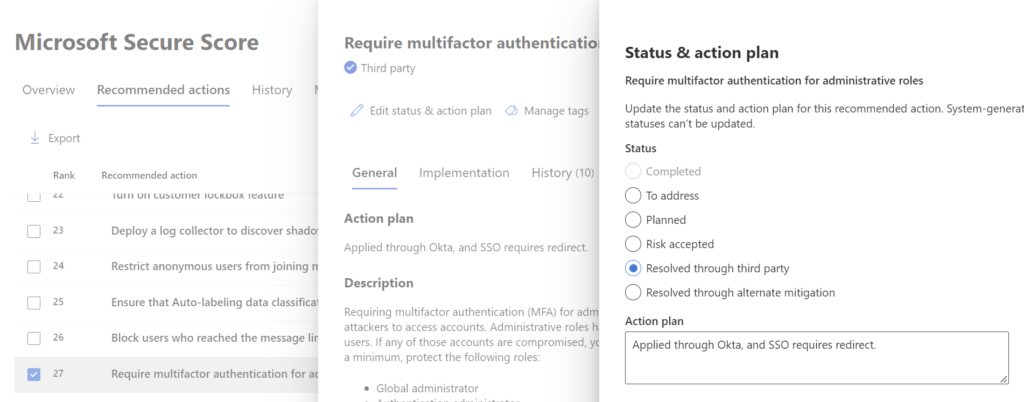
- Choose the control in the list of ‘Recommended Actions’
- On the summary break out page, click on ‘Edit status & action plan’
- Choose ‘Resolved through third party, add how to the Action Plan and click ‘Save’
Unrecognized Updates
As I mentioned earlier, I’ve experienced situation when I’ve implemented the recommended action but it is not properly recognized by the Microsoft Secure Score. More specifically this happens with controls recommending policies. Such as ‘Enable policy to block legacy authentication’ and ‘Publish M365 sensitivity label data classification label policies’ for example.
When this occurs, I recommend;
- Review you’ve implemented the control according to the documented ‘Implementation’ instructions.
- Remove, or delete your policy or control, save and exit. And reapply.
- Ensure you wait up to 48 hours, as that’s how long it can take Security Center to sync and recognize the change.
- Have a second person review and ensure the recommended action has been implemented correctly.
Then, if the score still doesn’t reflect the change, I recommend updating the control status with the ‘Edit status & action plan’. Here select ‘Resolved through alternative mitigation’ and then in the Action Plan documentation box record how you did it, and who reviewed it.
Conclusion
Having a process to ensure your cloud environment is secure and not mis-configured is critical to preventing exploits and data exfiltration. These attacks can have a crippling impact on organizations and in addition can often provide the data, credentials, and access to pivot further into the organization and do further damage by identifying all your vendors, partners, contacts, and emails.
Hopefully this process will help secure your Microsoft Azure, or Microsoft Office 365 cloud environment by achieving a high security score that reflects due diligence and responsibility.
This process of identifying actions and prioritizing them should take less than an hour. With the right technology culture, implementing all the available security recommendations should take less than a week of focus.
I recommend adding this security score to your cybersecurity metrics and reports to provide risk visibility to your leadership.


Recent Comments